Adworld Re Writeups
Reversing-x64Elf-100
下载附件得到.re文件.
先用DIE看看是什么文件:

然后再扔进IDA:
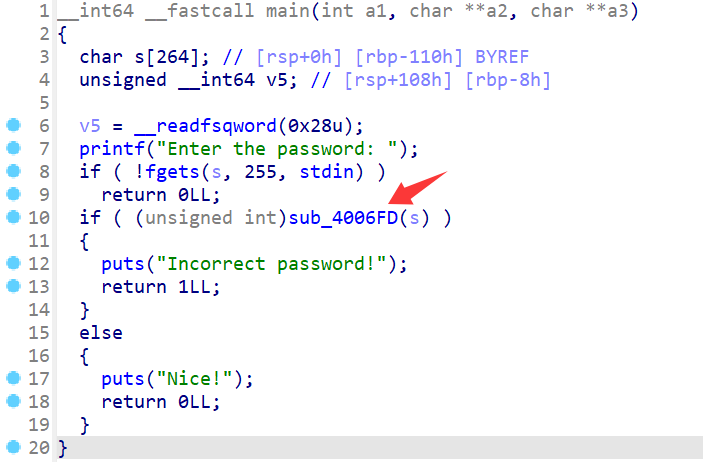
重点是这个sub_4006FD函数:
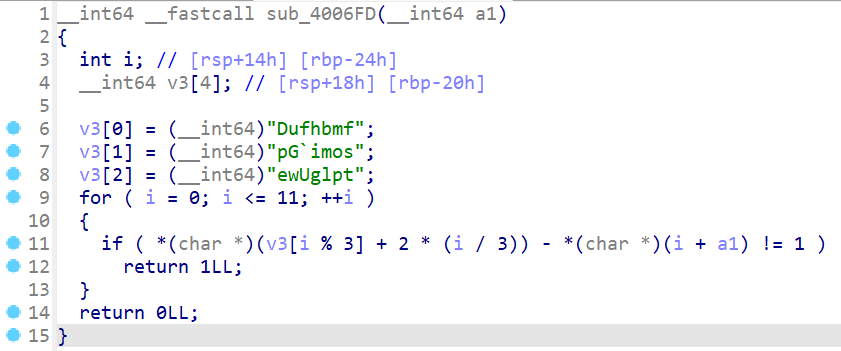
根本不需要分析, 直接打印*(char *)(i + a1)就行.
exp:
|
Flag: Code_Talkers
666
解压附件得到666文件.
DIE:
IDA:
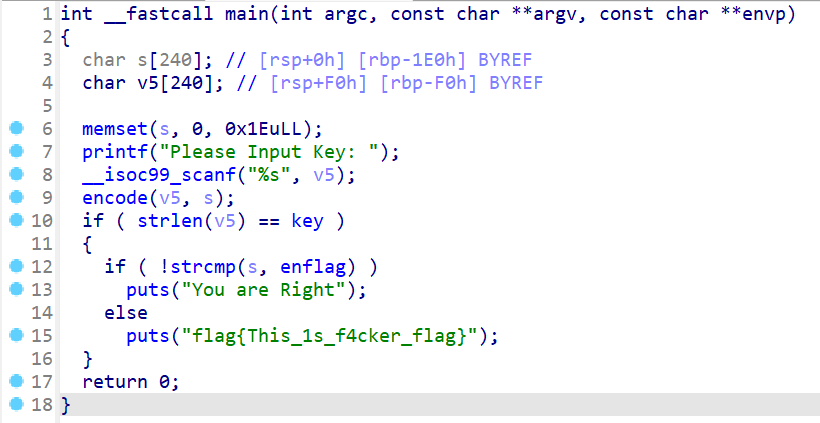
- main函数:
- encode函数:
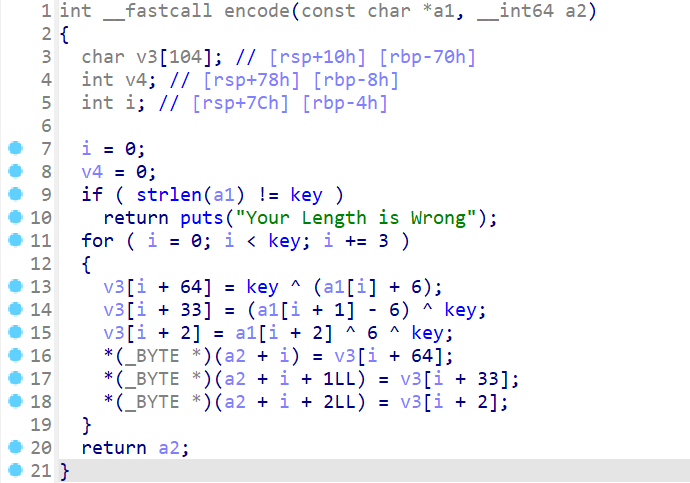
key=18,enFlag=izwhroz""w"v.K".Ni
encode是线性的, 而且只涉及简单的加减和异或, 直接逆就行了.
exp:
|
Flag: unctf{b66_6b6_66b}
easyRE1
解压附件得到easy-32和easy-64.
两个文件扔到IDA里是几乎一样的:
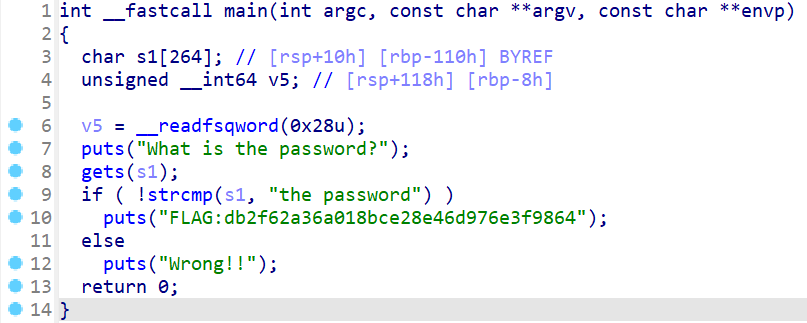
直接提交db2f62a36a018bce28e46d976e3f9864, 错误.
对db2f62a36a018bce28e46d976e3f9864进行解密无果, 直接搜这个字符串才知道答案要包上flag{}…
显然这是个签到题.
Flag: flag{db2f62a36a018bce28e46d976e3f9864}
lucknum
解压附件得到lucknum文件.
DIE:
IDA:
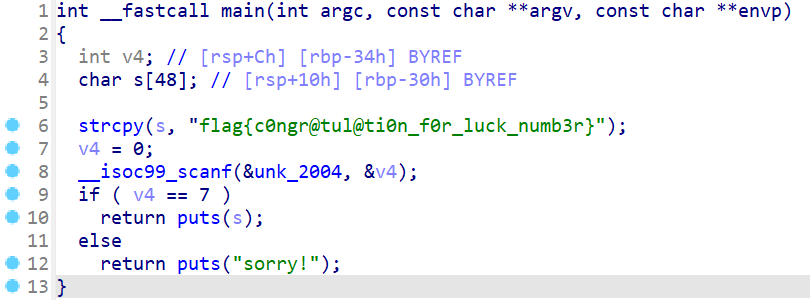
也是一道搞笑签到题.
Flag: flag{c0ngr@tul@ti0n_f0r_luck_numb3r}
reverse_re3
解压附件得到main2文件.
DIE:
IDA:
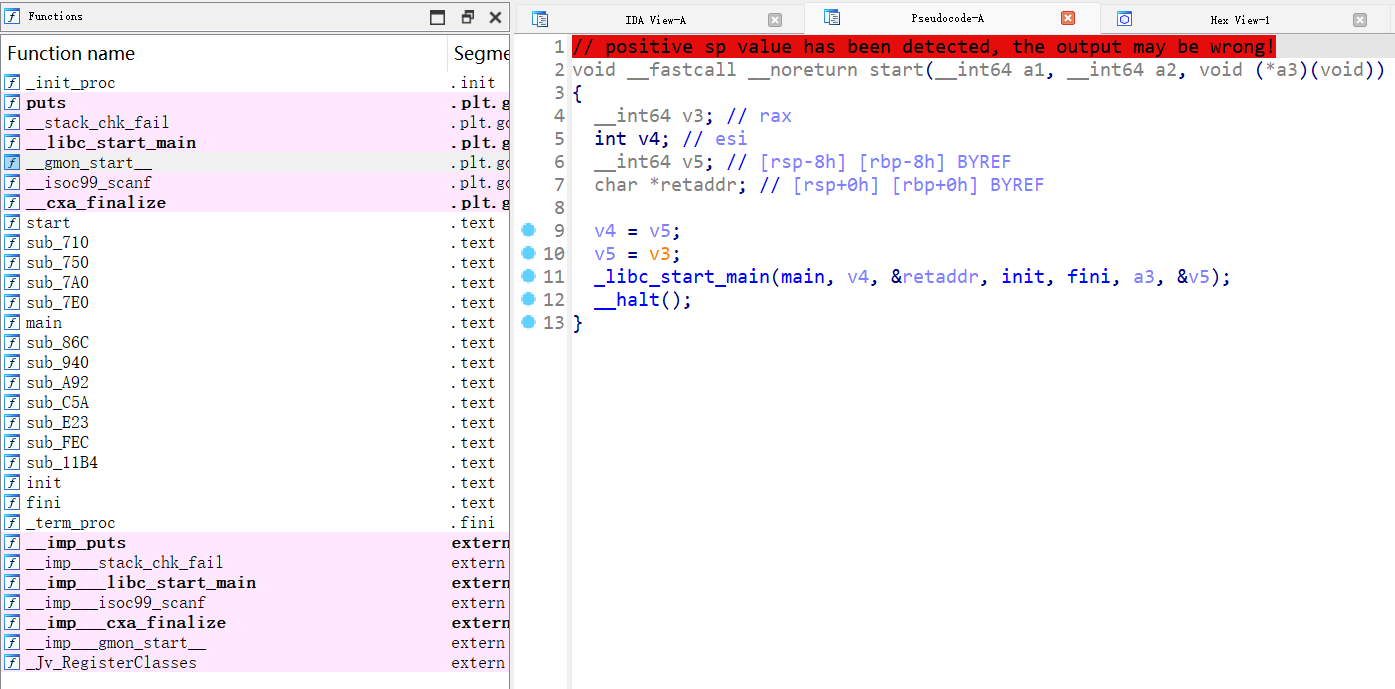
看到positive sp value has been detected.有点慌, 先切到main函数看看:
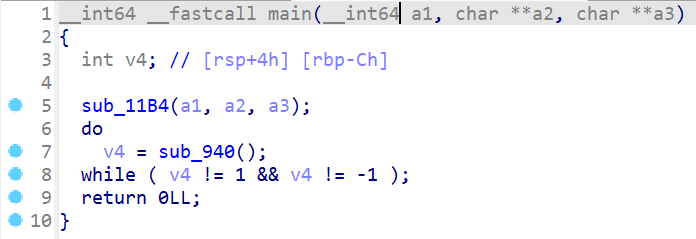
重点是这个sub_940函数:
__int64 sub_940() |
可以看出, 这应该是一个走迷宫程序, 再来看看sub_86C, sub_E23, sub_C5A, sub_A92, sub_FEC:
unsigned __int64 sub_86C() |
__int64 sub_E23() |
__int64 sub_C5A() |
__int64 sub_A92() |
__int64 sub_FEC() |
合理猜测dword_202AB4是横坐标, dword_202AB8是纵坐标, dword_202020是地图, dword_202AB0目前还不知道是啥.
看看dword_202020:
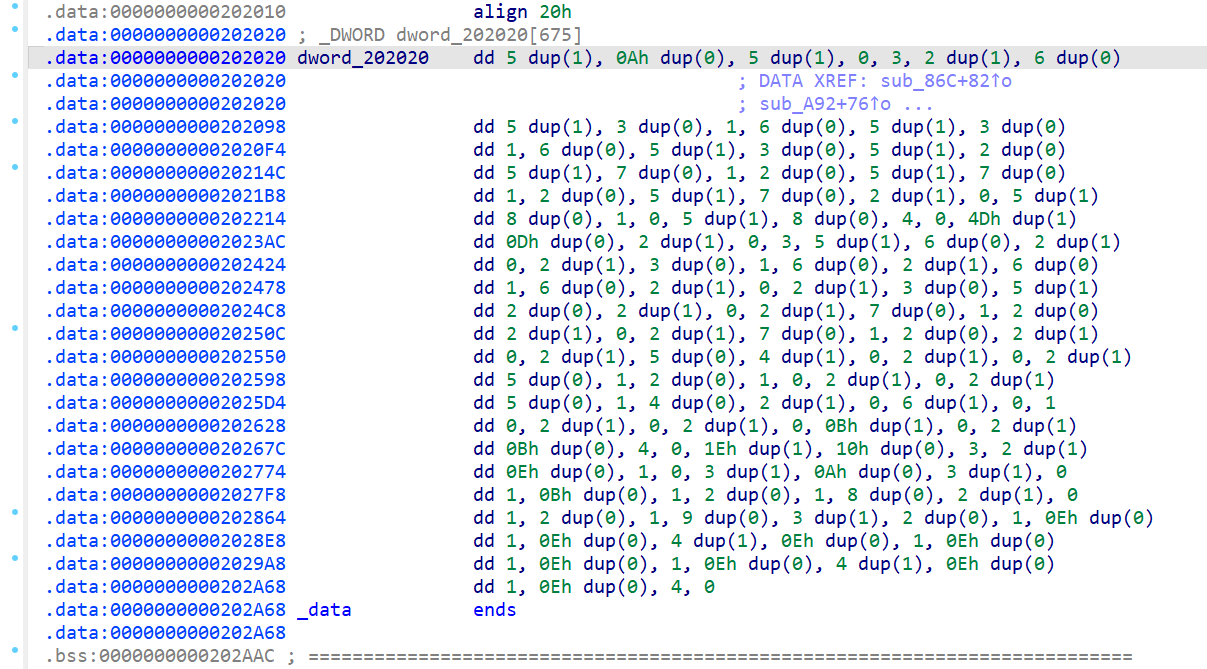
选中这个区段的数据, 按快捷键shift + E即可导出数据. 注意要选择initialized C variables: DWORD是双节, 相当于unsigned long.
dword_202020 (25行27列)
_DWORD dword_202020[675] = |
通过坐标的上下限, 很容易得知地图的大小是 dword_202020的大小是
上面这几个函数都能看到类似dword_202020[225 * dword_202AB0 + 15 * i + j]的语句, 可以大胆猜测: dword_202020其实是保存了dword_202AB0表示当前是第几个地图.
sub_940的循环终止条件: if(dword_202AB0 == 2) break; ++dword_202AB0;证实了这个猜测.
dword_202020 (3 * 15 * 15)
_DWORD dword_202020[3][15][15] = |
显然, 3代表起点, 4代表终点. 这里可以直接走, 但我还是写了个脚本来输出路线.
反正不是比赛, 怎样优雅就怎样来.
exp:
|
flag格式在sub_940的最后面: flag{md5(your input)}.
Flag: flag{aeea66fcac7fa80ed8f79f38ad5bb953}
1000Click
解压附件得到1000Click.exe.
DIE:
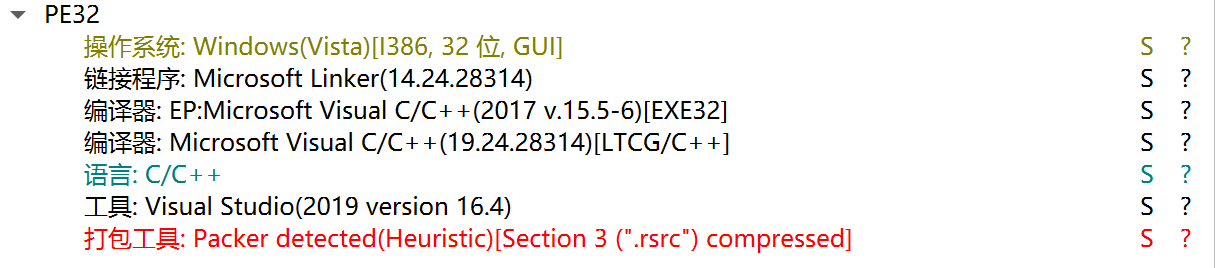
似乎加壳了. 用IDA打开, 发现有
果断放弃.
先用DIE直接查字符串:
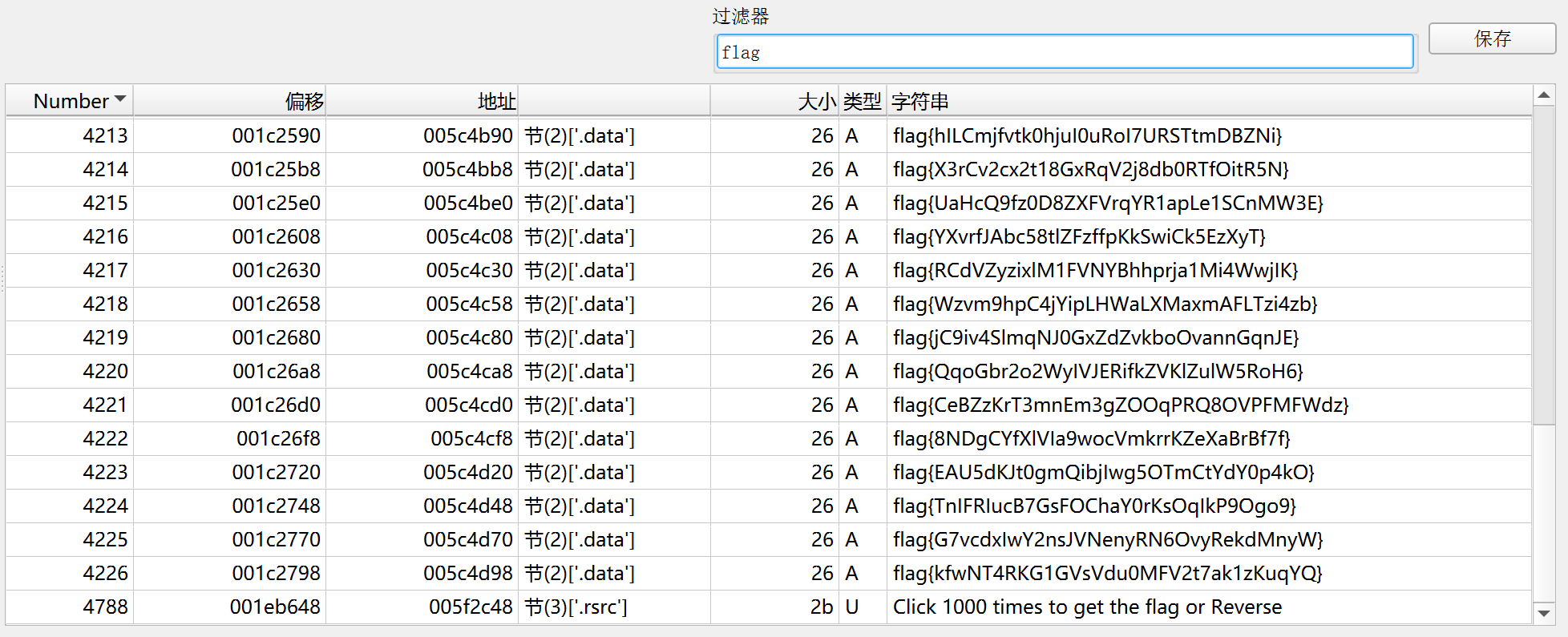
一堆假flag. 还是老老实实运行程序吧.
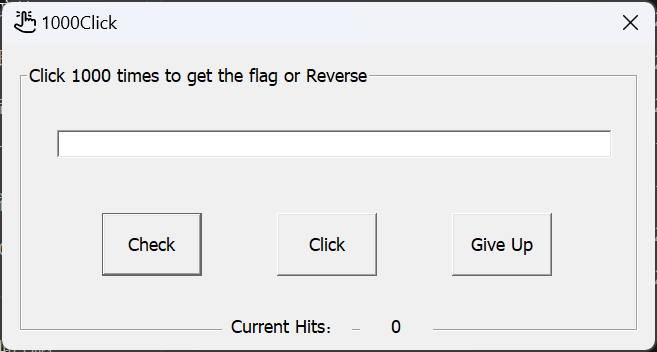
看样子, 只需要点击Click按钮
DBC或DC很快就点到
当然, 也可以写一个AutoClicker.
|
上述代码可能需要以管理员身份运行.
点击
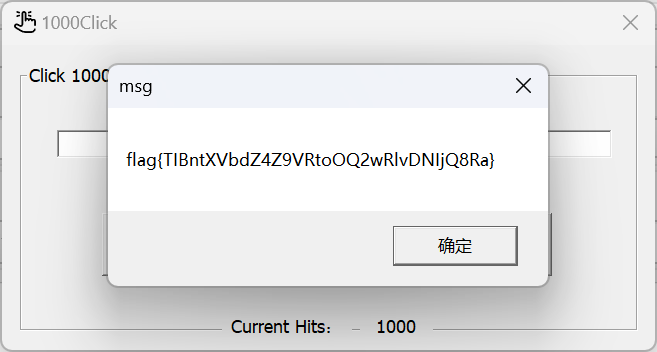
弹窗里的flag无法直接复制, 别傻呵呵地去辨认l和I, 直接在DIE里搜.
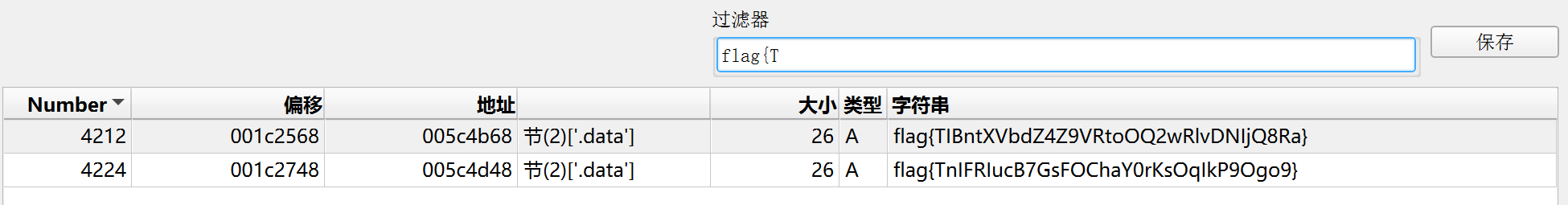
Flag: flag{TIBntXVbdZ4Z9VRtoOQ2wRlvDNIjQ8Ra}
crypt
解压附件得到 crypt.exe.
没有壳, 直接扔进 IDA 反编译.
int __fastcall main(int argc, const char **argv, const char **envp) |
__int64 __fastcall sub_140001120(_DWORD *a1, __int64 a2, int a3) |
_DWORD *__fastcall sub_140001240(_DWORD *a1, __int64 a2, int a3) |
分析了一下, 这是一个 RC4 加密.
Wiki: RC4
exp:
|
Flag: flag{nice_to_meet_you}
happyctf
附件是 happyctf.exe 与 happyctf.pdb.
把 happyctf.exe 扔进 IDA (32位), 发现主函数非常恶心:
int __cdecl main(int argc, const char **argv, const char **envp) |
重点是这个 lambda_1b3a4e77a09e1a7ed440bad3aa4c443b_::operator()(&add, item);, 跟进 add函数:
void __thiscall lambda_1b3a4e77a09e1a7ed440bad3aa4c443b_::operator()( |
发现似乎只是异或了一下 0x14.
于是, 将 key 与 0x14 异或, 即可得到 flag.
|
Flag: flag{Welcome_to_Neusoft}
xxxorrr
附件 xor, 扔进 IDA.
__int64 __fastcall main(int a1, char **a2, char **a3) |
unsigned __int64 sub_84A() |
unsigned __int64 sub_916() |
main 函数并没有显示调用 sub_84A 与 sub_916 函数, 但可以合理推测 sub_84A 在 main函数之前调用, sub_916 在 main 函数之后调用.
于是, 整个执行流程为: sub_84A 操作 s1[i] -> main 中 s1[i] 与 s[i] 异或 -> sub_916 要求 s1[i] 与 s2[i] 相同.
exp:
|
Flag: flag{c0n5truct0r5_functi0n_in_41f}
bad_python
做过类似题, 看一眼题目描述就知道是要修复 pyc 文件头.
010 Editor 打开一看, 果然如此.
附一份正常的 pyc 文件:
33 0D 0D 0A 25 F7 21 68 14 00 00 00 E3 00 00 00 |
把头部替换掉即可. 然后 uncompyle6 -o . pyre.cpython-36.pyc 反编译得到 py 文件.
# uncompyle6 version 3.9.2 |
是一个变种 TEA, 直接解就行.
exp:
from ctypes import * |
Flag: flag{Th1s_1s_A_Easy_Pyth0n__R3veRse_0}
ereere
附件 ere, 扔进 DIE 一看, wtf, MIPS 指令集?
于是决定先咕咕咕.
- 标题: Adworld Re Writeups
- 作者: Coast23
- 创建于 : 2025-01-26 16:37:08
- 更新于 : 2025-06-15 17:29:45
- 链接: https://coast23.github.io/2025/01/26/Adworld-Re-Writeups/
- 版权声明: 本文章采用 CC BY-NC-SA 4.0 进行许可。
